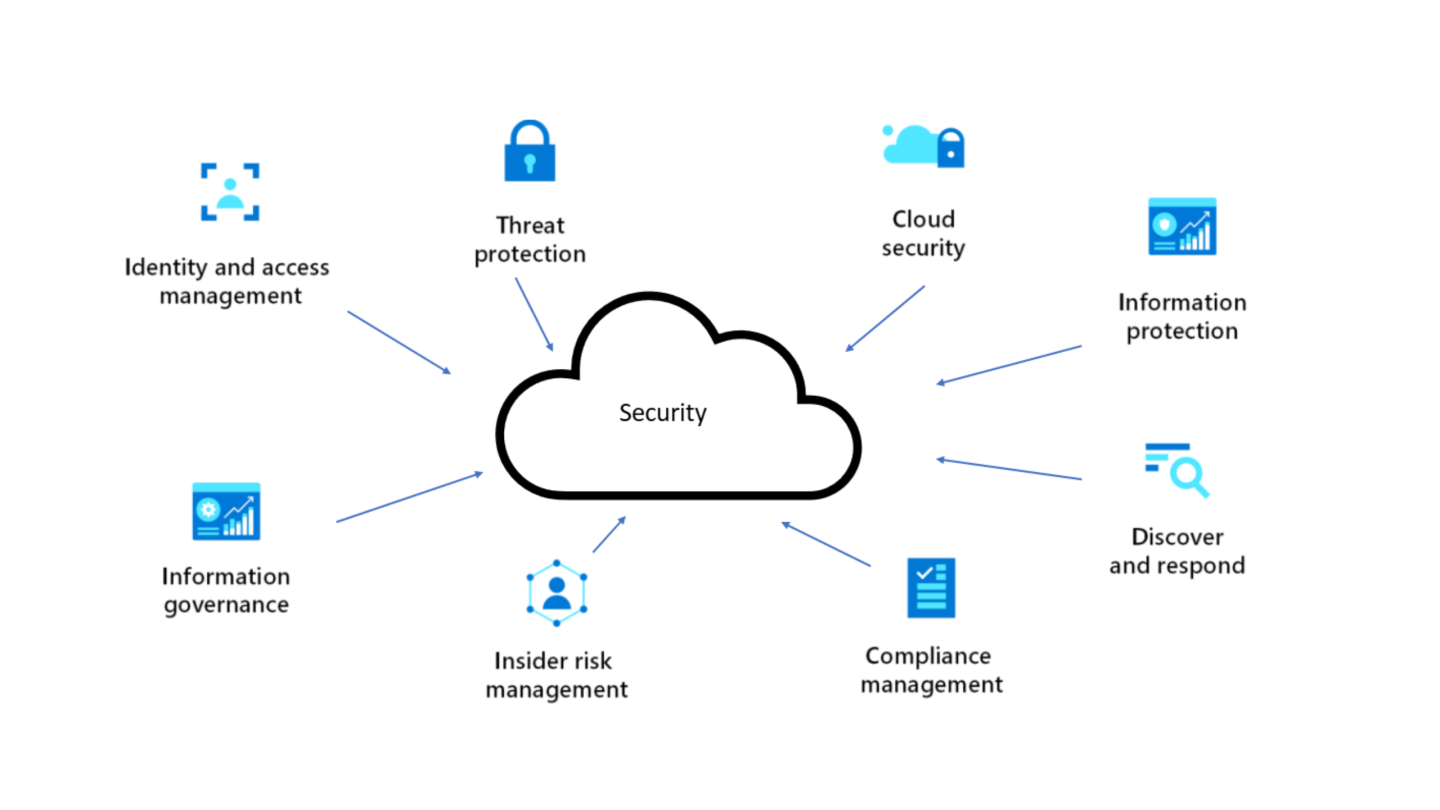
I will provide detailed assessments and solutions for security architecture
About This Jab
I will provide detailed assessments and solutions for security architecture
My services include a thorough analysis of your security architecture, ensuring that your systems are robust and compliant with best practices.
- Cloud Security Evaluation:
- Inspect cloud infrastructures for security flaws.
- Detect configuration errors and evaluate associated risks.
- Implementing Security Best Practices:
- Utilize encryption and robust authentication methods.
- Enhance security of cloud storage and databases by establishing access restrictions.
- User Access and Permissions Review:
- Apply the principle of least privilege and carry out regular audits.
- Implement role-based access control (RBAC) strategies.
- Review of Data Flow:
- Ensure data is encrypted during transmission and evaluate communication methods.
- Examine data retention and secure deletion protocols.
- Third-Party Security Assessment:
- Analyze third-party services for potential security vulnerabilities.
- Secure API integrations and external links.
- Compliance with Regulations:
- Ensure your architecture adheres to necessary regulations.
- Assist in preparing compliance documentation and audit reports.
Compare Packages
|
Basic
Expert Cloud Security Assessment and Guidance
99 €
|
Premium
Cloud Security Architecture Review and Advice
199 €
|
Deluxe
Comprehensive Cloud Security Architecture Assessment Call
498 €
|
|
| Delivery Time | 1 Day | 3 Days | 5 Days |
| Revisions | 2 Revisions | 3 Revisions | Unlimited |
| Automatic Scan | |||
| Secure Authentication | |||
| Asset Discovery |
About The Freelancer
My approach focuses on delivering value while ensuring your business's critical assets remain protected from cybersecurity threats. With experience in…
- Frankfurt
Frequently Asked Questions
How do you address security misconfigurations in the cloud?
I identify misconfigurations in your cloud setup and rectify them to ensure your environment follows security best practices. This includes securing cloud storage, databases, and ensuring proper access controls are in place.
What security best practices do you implement?
I apply encryption, strong authentication controls, and implement least privilege access principles. Additionally, I review and secure cloud storage and databases, ensuring all sensitive data is encrypted and properly protected.
Can you help with securing cloud storage and databases?
Yes, I ensure that your cloud storage and databases are secured by implementing access controls, encryption, and strong authentication mechanisms to prevent unauthorized access and data breaches.
What does the final report include?
The final report includes a comprehensive overview of the security gaps, recommended improvements, and a detailed action plan for securing your cloud environment. It also includes an evaluation of your compliance status with relevant regulations.
Recommended For You
Expert Cloud Security Assessment and Guidance 99 €
1 Day Delivery
2 Revisions
- Automatic Scan
- Secure Authentication
- Asset Discovery
Cloud Security Architecture Review and Advice 199 €
3 Days Delivery
3 Revisions
- Automatic Scan
- Secure Authentication
- Asset Discovery
Comprehensive Cloud Security Architecture Assessment Call 498 €
5 Days Delivery
Unlimited Revisions
- Automatic Scan
- Secure Authentication
- Asset Discovery